As well as dealing with known threats, service providers must be constantly vigilant against emerging and, as yet, unknown cybersecurity threats across an expanded threat surface. Automation is key to meeting this challenge.
Cybersecurity has always been a game of ‘cat and mouse’ between organisations (and consumers), and their adversaries. However, in recent years – with the growth of cloud computing, edge computing, IoT, network slicing, and more – the threat surface has expanded significantly. When organisations deploy threat protection, malicious actors seem to find a way around it.
At some point, Artificial Intelligence (AI) is also going to make that threat surface even more complex and dynamic – if it is not doing so already. It’s an on-going challenge for all organisations, governments, and individuals.
Is cybersecurity getting easier or harder?
According to the annual ‘State of Security’ report from Splunk, many organisations feel that cybersecurity is becoming less of a challenge (see Figure 1)[1]. As shown, 41% of organisations consider it to be easier in 2024 than in 2022 (compared to 17%). Splunk puts this down to much greater collaboration and more stringent compliance requirements.
Figure 1. Is cybersecurity becoming easier?
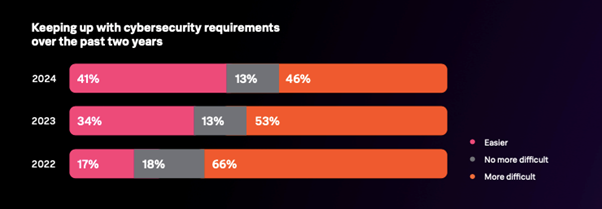
Source: Splunk
The expanding threat landscape was cited by 38% of respondents who felt that cybersecurity was becoming more demanding. The deployment of Massive IoT, edge computing, 5G Standalone and network slicing, and the significant growth of cloud computing represent new threat surfaces for malicious actors while increasing data volumes exponentially. This means that organisations must adopt a holistic, proactive, continual security strategy and mindset to protect against as yet unknown cybersecurity threats. Of course, any single security vulnerability at any end point in the network can enable malicious actors to breach protection and then move laterally throughout the network.
This threat surface includes connected devices that may be accessing SharePoint or Kerberos, for example, that can if breached can be used to access personal and organisational data, including One-Time Passwords, APIs, personal data, session cookies and tokens, and so much more.
As well as malicious actors and organised criminals, state-backed attacks are becoming more frequent. Also, basic human error and misconfigurations of devices, such as smartphones, smart meters, and smart home-connected devices are an easy target for adversaries.
Likewise, human errors in the implementation of organisational policies, systems, or configurations add to the problem (which in fact ranked as the top challenge for organisations in the Splunk 2024 survey).
A more complex compliance landscape
In addition, more stringent compliance obligations – such as the European Union’s NIS 2 Directive and the UK’s Telecoms (Security) Act 2021 – further add to the burden.
While NIS 2 requires much stronger reporting requirements – requiring information about emerging threats to be quickly shared between organisations (and governments) throughout the region – cybersecurity is a constantly evolving game.
Generative AI is likely to raise the stakes further. According to the Splunk survey, 45% of respondent predicted that ‘adversaries’ would benefit the most from the technology, compared to 43% who believe ‘defenders’ will come out on top through the use of AI for cybersecurity purposes. Of course, adversaries are unencumbered by legislation and compliance obligations, so it remains to be seen.
The point is that cybersecurity is a constantly evolving landscape. That’s why regulations such as NIS 2 demand an on-going, proactive approach to security, which includes holistic, cross-domain policies, as well as education for employees, and continuous security audits and testing. It also demands rapid reporting of all threats, especially emerging threats, so that information can be easily shared.
Automation and AI against security threats: A symbiotic relationship
There is no doubt that AI will help, but it may take some years to mature and to see the benefits. Right now, automation is benefitting organisations in their fight against hackers and security attacks. It is fully future proof, as in time automation and AI will form a powerful symbiotic relationship in the cybersecurity fight.
The We Are CORTEX automation platform provides a cross-domain approach to security. It can provide continual monitoring, testing, and reporting of security behaviours and potential attacks, meaning that it not only protects your applications, systems, network, and consumers, it also enables compliance to give you peace of mind.
It provides an incremental approach to security automation, including sub-processes, processes, legacy systems, cloud and edge computing, and domains and can bring significant business benefits right now. Automation also supports the path towards full AI/Automation integration.
CORTEX offers a holistic, incremental approach to cybersecurity, eliminates human error and requires no human intervention. It can provide regular security auditing, testing, and reporting, as well as on-going, continual monitoring of any anomalous network patterns and behaviours, enabling rapid identification of existing and emerging cybersecurity threats. It enables you to guard against today’s known threats – and to construct defences against tomorrow’s unknown risks.
Start your journey now by contacting us today.
[1] https://www.splunk.com/en_us/form/state-of-security.html







