The recent enactment of the European Union’s NIS 2 Directive places a compliance burden on telcos throughout the region – as well as strict reporting requirements. How can automation ensure your compliance?
The European Union’s NIS 2 Directive was enacted into law on 17th October 2024 and requires an over-arching, holistic approach to cybersecurity. Siloes of security domains are not an option, because a cross-domain strategy is baked into the legislation. Likewise, the UK’s Telecoms (Security) Act (TSA) 2021 became law in that year.
Both are aimed at protecting and securing the resilience of national communications infrastructure and represent significant compliance obligations for organisations throughout the region. NIS 2 aims to boost OT security, simplify reporting, create consistent rules and penalties, and, in the long run, strengthen European organisations’ security.
Are you an “Essential” or “Important” entity in NIS 2?
Importantly, compliance with the TSA does not necessarily lead to compliance with NIS 2, but both place a significant burden on UK and European organisations. So, it’s essential to put the right policies, strategies, and systems in place to avoid significant fines and damage to reputation.
The first port of call is to understand where your organisation sits on the NIS 2 criticality framework. NIS 2 divides organisations into three types:
- “Essential” (compliance is an obligation)
- “Important’ (which applies some requirements placed on Essential entities, but not all)
- “Not in Scope” (which means there are no obligations to comply, but adoption of the framework is recommended to ensure security resilience). Each sector is likely to face different vulnerabilities
Table 1 sets out the sectors that fall into each section.
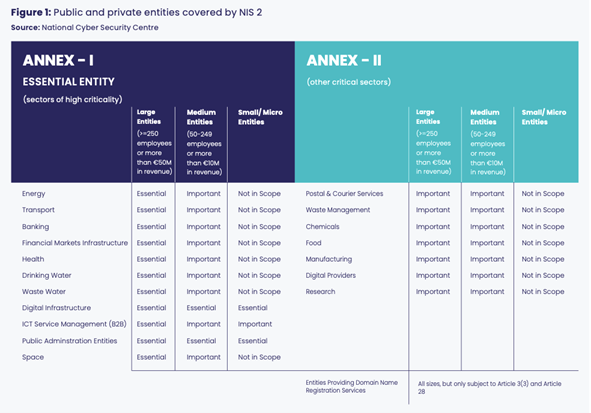
Source: National Cyber Security Centre
NIS 2 builds on the original NIS Directive and expands the types of organisations and sectors included, while spelling out the requirements for the reporting of security breaches. It also demands an on-going, proactive approach to cybersecurity.
The NIS 2 Directive timeline. Don’t be late!
The legislation also requires Member States to establish at least one Computer Security Incident Response Team (CSIRT). These groups are in place to assess, report on, and respond to any reported cyber incident or threat so that networks can recover quickly and share information throughout region, to avoid similar or future attacks.
On 17th January 2025, CSIRTs throughout the EU are expected to assess and report on the progress of NIS 2 Directive compliance and operational cooperation – i.e., has your organisations put appropriate measures in place?
By 17th April 2025, each Member State is expected to have compiled a list of entities, which should have been placed into either Essential or Important categories by that date.
By 17th October 2027, the Directive is expected to be amended and updated in order to ensure that new and emerging threats, or requirements, are put in place. It means that organisations have their work cut out to ensure compliance an on-going basis.
As you can see, there are a series of deadlines to meet – and not much time in which to do so.
Another issue that, as well as traditional security threats such as DDOS, espionage, and supply chain disruptions, the threat surface is expanded rapidly and growing in complexity. For example, smartphones and laptops or IoT-connected machines mean that the threat landscape has expanded to the edge of the network.
In addition, many devices may also access other data applications, on a smartphone for example, expanding the threat surface further. Are they sharing data with other applications, for example? What about remote working? Are the dynamic network slices made that are being introduced with 5G Standalone vulnerable – on an on-going and continually shifting basis?
A holistic, automated approach to NIS 2 compliance
A holistic, proactive approach to compliance is not only essential for operational integrity, but it is also a requirement of the NIS 2 Directive.
Traditionally, many operators and service providers have applied a domain-based approach to the different threats. However, this can lead to siloes of security protection, as well as gaps in the broader approach to cybersecurity today that is required to counter ever-more sophisticated and complex threats and attacks across an expanded attack surface. How can you meet this challenge?
Automation may not spring immediately to mind, but it is an essential tool in not only meeting your compliance obligations, but also your reporting requirements. For example, it helps with sharing information – and, in turn, to build a more resilient and secure Europe-wide network infrastructure for all.
Automation can help to track events and actions that could lead to vulnerabilities or are signs of emerging attacks. It also eliminates human error, while providing the visibility into a chain of actions and inputs that can be collected and correlated from disparate systems, across all domains, to ensure you meet your reporting obligations too.
The We Are CORTEX automation platform can help you to meet all of your NIS 2, and TSA, obligations, without human intervention or error, and provide a consolidated, correlated view of your security threat landscape.
The elements of the platform can be reused, amended, added, and strictly controlled by only authorised personnel, ensuring your peace of mind.
To find out more – and how you can keep pace with the demanding timetable, download our paper by clicking below, or get in touch today.







